How Legba's Browser-Native Isolation Actually Protects You: A Technical Deep Dive
A technical deep dive into how Legba's browser-native isolation actually works—from edge-based execution to ephemeral containers to threat-by-threat protection.
Introduction: The Browser Security Problem Demands a Different Architecture
Here's the uncomfortable truth: 85% of your workday happens in a browser, yet 60% of all security breaches originate from that exact attack surface. The place where you do your most critical work is also the place where traditional security completely fails.
Your antivirus can't stop browser-native ransomware. Academic research proved it bypassed AVG, Kaspersky, Avast, Malwarebytes, and TrendMicro without breaking a sweat. Your firewall? Useless against encrypted HTTPS traffic carrying zero-day exploits. Your VPN? It creates an encrypted tunnel, but the browser-based threat travels safely inside it, waiting to execute on your endpoint.
The numbers tell a grim story:
- 68% of successful ransomware attacks originate in the browser
- 92% of users clicked a phishing link within the last year
- 147,000 token replay attacks detected by Microsoft in 2023 alone (a 111% year-over-year increase)
- 75 zero-day vulnerabilities exploited in the wild in 2024, with 7 specifically targeting Chrome
- $33.7 million in fraud losses from session hijacking annually
Traditional security architecture assumes you can protect the endpoint. Browser-based threats proved that assumption catastrophically wrong.
We built Legba because the security industry needed a fundamentally different approach. Not another signature database. Not another AI-powered detection engine. An architecture where browser-based threats simply cannot reach your systems, regardless of how sophisticated, novel, or polymorphic they are.
This is the technical breakdown of how Legba's browser-native isolation actually works.
85% of work happens in browsers. 60% of breaches start there. Yet most security solutions still focus on protecting the endpoint. Browser isolation flips the entire security model. Here's how it works:
— Aakash Harish (@0_Aakash_0) November 10, 2025
What Is Browser-Native Isolation? (The Conceptual Foundation)
The Traditional Browsing Model: Trust Everything
In the traditional browsing model, here's what happens when you click a link:
- Your browser requests content from a web server
- The server sends HTML, JavaScript, CSS, images, and executable code
- All of that code executes directly on your device
- The JavaScript has access to your local resources (with permission)
- Downloads can access your file system
- Browser extensions can intercept your credentials
- Malicious code can exploit browser vulnerabilities to break out of the sandbox
This model assumes every website is trustworthy, every piece of JavaScript is benign, and every browser vulnerability is patched before attackers exploit it. Reality has proven all three assumptions false.

The Isolation Model: Trust Nothing, Execute Elsewhere
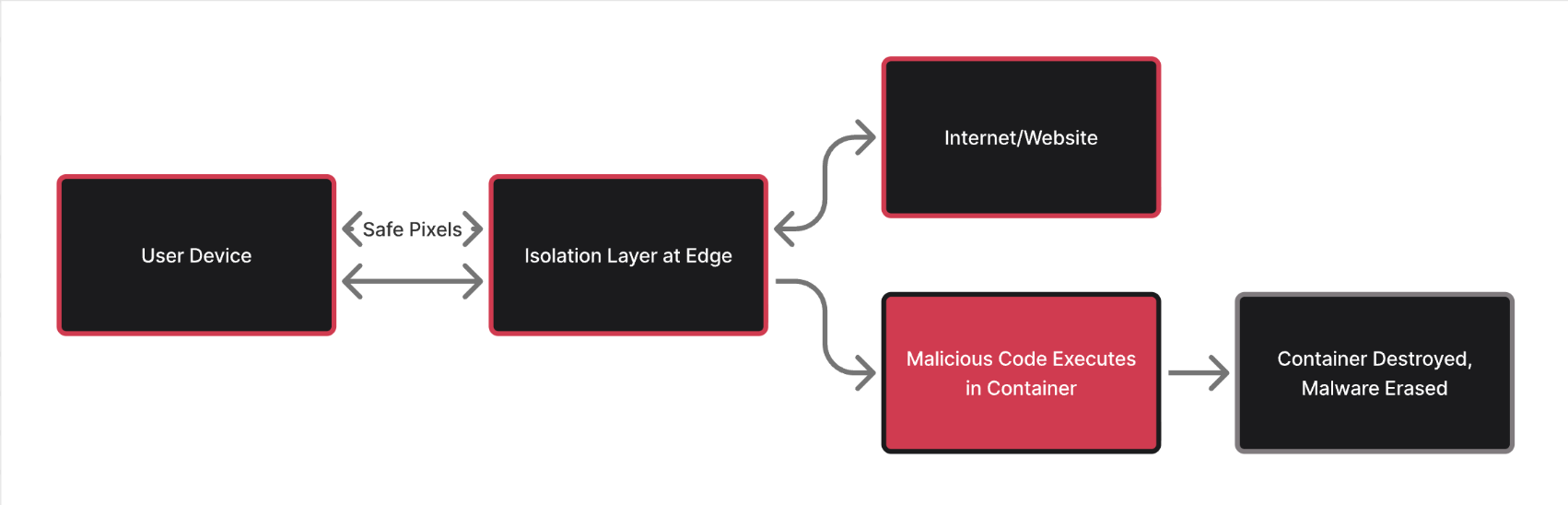
Browser isolation inverts that model. Instead of executing web content on your device and hoping it's safe, isolation executes everything in a separate environment and only delivers safe content to your endpoint.
Think of it as an air gap, but for your browsing session.
Here's the fundamental difference:
Traditional browsing: Website → Your Device → Execution → Malware on Your System
Isolation browsing: Website → Isolated Container → Execution → Safe Visual Stream → Your Device
The malicious code executes. The zero-day exploit works. The ransomware encrypts files. But it all happens in an isolated environment that gets destroyed when you close the tab. Your actual device never sees executable code.
Remote Browser Isolation vs. Browser-Native Isolation: Why the Difference Matters
There are two approaches to isolation, and understanding the difference is critical:
Remote Browser Isolation (Traditional RBI):
- Executes browsing sessions on centralized cloud servers (often hundreds or thousands of miles away)
- Streams rendered pixels back to your device
- Creates significant latency (200-500ms added to every interaction)
- Requires massive centralized infrastructure
- Degrades user experience to the point where employees disable it
Browser-Native Isolation (Legba's Approach):
- Executes browsing sessions at the network edge (geographically close to users)
- Leverages distributed edge computing architecture
- Delivers native performance with imperceptible latency (<20ms overhead)
- Scales seamlessly without centralized bottlenecks
- Invisible to users while providing complete protection
The key innovation is where the isolation happens. Traditional RBI centralizes execution in distant data centers, creating the latency that makes users hate it. Legba distributes execution to edge nodes near users, delivering the security of isolation with the performance of native browsing.
This isn't a minor technical detail. It's the difference between a security solution employees circumvent and one they never notice.
Legba's Architecture: Edge-Based, Not Cloud-Based
The Problem with Traditional RBI: Distance Creates Latency
Traditional remote browser isolation has a physics problem. When you click a link, here's what happens:
- Your request travels to a centralized cloud data center (let's say it's 800 miles away)
- The data center fetches the website content
- The data center renders the page in an isolated browser instance
- The data center compresses the rendered pixels
- The compressed video stream travels 800 miles back to you
- Your browser decodes and displays the stream
Even at the speed of light, that 1,600-mile round trip adds latency. In practice, traditional RBI adds 200-500ms of lag to every interaction. Pages load slowly. Videos stutter. Forms feel unresponsive.
Users notice. And what users notice, they disable.
Legba's Edge Approach: Distributed Execution, Minimal Latency
Legba's architecture is fundamentally different. Instead of centralizing isolation in distant cloud data centers, we distribute it to edge nodes positioned near users.


The difference is 70ms of added latency versus 10ms. In practice, edge-based isolation feels identical to native browsing. Cloud-based isolation feels sluggish enough that users complain.
Technical advantages of edge computing for isolation:
- Geographic proximity reduces round-trip time: Edge nodes are typically 10-50ms away instead of 50-200ms
- Distributed load prevents bottlenecks: No single data center becomes overwhelmed during peak usage
- Local caching improves performance: Frequently accessed content can be cached at the edge
- Resilience through redundancy: Multiple edge nodes provide failover and load balancing
- Scalability without infrastructure overhaul: Adding capacity means deploying more edge nodes, not rebuilding centralized infrastructure
This is why Legba's tagline is "Invisible by Design." The security is absolute, but the user experience is indistinguishable from native browsing.
How Legba Works: Step-by-Step Technical Breakdown
Let's walk through exactly what happens when you browse the web with Legba protecting you. We'll use a concrete example: you receive an email with a link to what appears to be a Google Docs file, but it's actually a phishing site hosting browser-native ransomware.

Step 1: Browser Extension Deployment
Before any browsing happens, your IT administrator deploys Legba via a Chrome extension. This is a critical architectural decision.
Why a Chrome extension?
- No network reconfiguration required: Unlike traditional RBI solutions that require proxy configurations, DNS changes, or network appliance installations, Legba deploys as a simple browser extension
- Rapid rollout: IT administrators can push the extension to thousands of users via Google Workspace in minutes, not months
- No specialized hardware: No on-premise servers, no network appliances, no infrastructure investments
- Transparent to users: The extension operates invisibly; users browse normally while Legba protects them
The extension is lightweight (under 2MB) and requires no user configuration. Once installed, it immediately begins intercepting and protecting all web requests according to centrally defined policies.
Step 2: Request Interception and Policy Evaluation
You click the suspicious link in your email. Here's what happens at the technical level:
- You click the link:
https://docs-google-secure-share.com/document/d/malicious - Legba's extension intercepts the request before it reaches the actual website
- The extension evaluates the URL against your organization's isolation policies:
- Is this domain on the trusted internal domain list? (No)
- Is this a known high-risk category (document sharing, external collaboration)? (Yes)
- Does the user's role require isolation for external links? (Yes)
- Should this request be executed locally or in isolation? (Isolation required)
This policy evaluation happens in milliseconds, completely transparently. The extension makes the decision based on centralized policies configured by your security team.
Policy examples:
- Isolate all external websites for executive users
- Isolate all file-sharing and collaboration tools
- Isolate any domain not on the corporate whitelist
- Isolate any website flagged by threat intelligence feeds
- Always isolate for unmanaged/BYOD devices
The power of this approach is granularity. Your security team can define exactly which browsing activities require isolation based on user role, device posture, risk classification, and contextual factors.
Step 3: Edge-Based Execution in Ephemeral Container
The extension has determined that this request requires isolation. Now the technical magic happens.
Request redirection to edge node:
- Legba redirects your request to the nearest edge node (let's say it's 15ms away in your metropolitan area)
- The edge node spins up an ephemeral container specifically for your browsing session
- The container is completely isolated:
- Fresh browser instance with no persistent state
- Virtualized file system with no access to real storage
- Isolated network stack
- Separate process space
- No access to your actual credentials, cookies, or session tokens
The malicious website loads in the isolated container:
- The edge node fetches
https://docs-google-secure-share.com/document/d/malicious - The malicious site serves its payload: JavaScript that exploits a zero-day Chrome vulnerability and delivers browser-native ransomware
- The exploit executes successfully (this is important: we're not trying to detect or block the malware)
- The ransomware begins encrypting files using the File System Access API
- It encrypts everything in the container's virtualized file system
Here's the critical point: All of that attack activity happens in the isolated container. The zero-day exploit works. The ransomware runs. Files get encrypted. From the attacker's perspective, the attack succeeded.
But the "files" being encrypted exist only in the ephemeral container. Your actual files on your actual device are untouched. The container's file system is virtualized and disposable.
Step 4: Pixel-Perfect Streaming to Your Device
While the malicious code executes in isolation, you need to see the web page. Legba handles this through pixel-perfect streaming technology.
How streaming works:
- The isolated browser instance renders the web page just like your local browser would
- Legba captures the rendered output as a visual stream (not executable code)
- The visual stream is compressed using efficient video codec technology
- The stream is transmitted to your device via an encrypted channel
- Your browser displays the stream in a canvas element that looks and feels identical to a native web page
What you see: A perfectly rendered web page that responds to your inputs normally
What's actually happening: You're viewing a real-time video stream of a web page executing in an isolated container 15ms away
The streaming technology is so sophisticated that you cannot tell the difference. Mouse movements, keyboard inputs, scroll events, video playback, interactive elements all work exactly as they would in native browsing.
Critical security point: Only rendered pixels reach your device. No JavaScript executes locally. No executable code downloads to your system. No malicious payloads touch your endpoint.
The ransomware is busy encrypting files in the isolated container. You're viewing a pixel stream of a web page. The attack cannot bridge that gap.
Step 5: Ephemeral Container Destruction
You realize the Google Docs link looks suspicious (the URL domain is weird), so you close the tab. Here's what happens:
- You close the browser tab displaying the isolated session
- Legba immediately destroys the ephemeral container:
- The isolated browser instance terminates
- All memory is released and cleared
- The virtualized file system is deleted
- All session cookies, cache, and tokens are erased
- All malware that infiltrated the container: gone
- The next time you browse, you get a completely fresh container:
- New browser instance
- Clean file system
- No persistent state from previous sessions
- No possibility of malware surviving across sessions
This ephemeral model is the ultimate defense against persistence. Even if malware successfully compromises the isolated environment, it cannot survive the session. There's no registry to modify, no startup folder to infect, no persistent storage to hide in.
Every browsing session is born clean and dies completely.
Forensic benefit: Because containers are ephemeral, Legba can optionally preserve them for forensic analysis when suspicious activity is detected. Your security team can examine the exact state of the container, including all malware payloads and attack artifacts, without any risk to production systems.
Application-Agnostic Protection: Beyond Just Browsers
Here's where Legba diverges from traditional browser isolation solutions: we don't just isolate browsers. We isolate any application requiring remote access.
The Security Gap in Browser-Only Isolation
Traditional RBI solutions protect web browsing. That's valuable, but it leaves massive security gaps:
- Email clients: What happens when you click a malicious link in your desktop email client?
- Chat applications: Slack, Teams, Discord all render links and can execute malicious content
- SSH/RDP access: How do you securely access internal systems from unmanaged devices?
- Internal web applications: Corporate portals, legacy apps, specialized tools
- File sharing: Dropbox, Box, OneDrive can all serve malicious content
If your isolation solution only protects browsing, attackers simply target the gaps.
Legba's Application-Agnostic Architecture
Legba extends isolation to any application that needs secure remote access. The same edge-based, ephemeral container architecture that protects your browsing also protects:
Email clients:
- Email rendered in isolated environment
- Links clicked within emails execute in isolation
- Attachments opened in isolated containers
- Credential entry happens in isolation (protecting against phishing)
- Local email client and credentials never exposed
Chat and collaboration tools:
- Messages rendered in isolation
- Links shared in chat execute in isolated containers
- File previews happen in isolation
- Screen sharing doesn't expose local system
- Malicious payloads can't escape the isolated environment
Internal web applications:
- Legacy corporate apps accessed through isolation
- No VPN required (isolation provides secure access)
- Zero Trust access model: verify identity, isolate execution
- Perfect for contractor and third-party access
SSH and RDP:
- Terminal access in isolated environment
- RDP sessions run in isolation
- Clipboard isolation prevents data exfiltration
- Credential theft can't compromise local systems
- Secure access from unmanaged devices without endpoint risk
Why This Matters: Comprehensive Attack Surface Reduction
Attackers are opportunistic. If they can't compromise you through Chrome, they'll try Outlook. If they can't phish you via email, they'll target Slack. If they can't exploit your browser, they'll target your SSH client.
Application-agnostic isolation eliminates the gaps. Every application that accesses external content or provides remote access runs in isolation. Your attack surface doesn't shrink, it effectively disappears.
Threat-by-Threat: How Legba Stops What Others Can't
Let's examine specific attack scenarios and walk through exactly how Legba's architecture prevents compromise. These aren't theoretical threats; these are real attacks happening right now that bypass traditional security.
Zero-Day Browser Exploits (75 Exploited in 2024)
The threat: Attackers discover and exploit browser vulnerabilities before vendors can patch them. Google Threat Intelligence Group tracked 75 zero-day vulnerabilities exploited in the wild in 2024, with 7 specifically targeting Chrome. These exploits bypass all signature-based detection because the signatures don't exist yet.
Traditional security response:
- Antivirus: Can't detect unknown exploits
- Endpoint detection (EDR): Might detect post-exploitation activity, but the initial compromise succeeds
- Web application firewalls: Can't inspect encrypted HTTPS traffic where exploits hide
- Browser sandboxing: Periodically bypassed by sophisticated exploits
How Legba stops zero-day exploits:
- Attacker crafts exploit for unpatched Chrome vulnerability (let's say CVE-2025-XXXXX, a use-after-free in the V8 JavaScript engine)
- Exploit code embedded in weaponized website (maybe disguised as a legitimate news article)
- User visits the malicious site while protected by Legba
- Legba redirects the request to isolated container at the edge
- The website loads in the isolated Chrome instance
- The exploit executes successfully:
- The V8 vulnerability is triggered
- Arbitrary code execution achieved
- The attacker has compromised the browser
- But the compromised browser is in the isolated container:
- Cannot access the user's actual file system
- Cannot access local network resources
- Cannot persist beyond the browsing session
- Cannot access real credentials or session tokens
- User closes the tab, container destroyed:
- The compromised browser instance terminates
- All exploit artifacts erased
- Next browsing session gets a fresh, unexploited container
The result: The zero-day exploit worked perfectly from a technical perspective, but it accomplished nothing. The attacker compromised an ephemeral container that existed for 3 minutes and then vanished. Your actual system was never exposed to the exploit code.
This is the fundamental power of isolation: You don't need to detect or block the threat. The threat can succeed completely, and it still can't harm you because it's succeeding in a disposable environment that has no access to anything valuable.
Browser-Native Ransomware: The Antivirus Bypass
The threat: Academic research from Florida International University demonstrated ransomware that executes entirely within the browser using the File System Access API and WebAssembly. This ransomware bypassed AVG, Kaspersky, Avast, Malwarebytes, and TrendMicro because it doesn't behave like traditional ransomware that endpoint security tools expect.
How it works:
- User visits malicious website (via phishing email, malicious ad, compromised legitimate site)
- Malicious JavaScript requests access to local files via File System Access API
- User grants permission (social engineering: "Please grant access to view your documents")
- WebAssembly encryption engine executes in the browser
- Files encrypted directly from the browser without any malware installation
- Ransomware note displayed, payment demanded
Traditional security response:
- Antivirus: Doesn't detect browser-based encryption as malicious behavior
- Endpoint protection: Can't distinguish legitimate browser API usage from malicious usage
- Firewalls: Can't inspect encrypted browser communications
- User awareness training: Relies on users recognizing and denying file system access requests (92% of users clicked phishing links in the past year)
How Legba stops browser-native ransomware:
- User visits the malicious website
- Legba isolates the website in an edge container
- The ransomware JavaScript executes in the isolated browser
- File System Access API requests granted (either through user permission or automated policy)
- WebAssembly encryption engine runs:
- Encrypts files in the container's virtualized file system
- All encryption happens in isolation
- User's actual file system is never accessible
- The ransomware displays payment demand
- User closes the browser tab
- Container destroyed, including all "encrypted" files
The result: The ransomware encrypted files successfully, but those files existed only in the ephemeral container. The user's actual documents, photos, and data were never accessible to the malicious code. The attack succeeded technically but failed practically.
Session Hijacking and Token Replay (147,000 Attacks, $33.7M Cost)
The threat: Modern session hijacking has evolved beyond network sniffing. Attackers now use malware, phishing, and browser exploitation to steal session tokens and cookies, then replay them to access cloud applications and services. Microsoft detected 147,000 token replay attacks in 2023, representing a 111% year-over-year increase. Average fraud losses reach $7.5 million annually, with investigation costs adding another $26.2 million.
Attack scenario:
- User authenticates to corporate SaaS application (Microsoft 365, Salesforce, etc.)
- Browser stores session token/cookie
- Attacker compromises the endpoint or browser (via malware, zero-day exploit, malicious extension)
- Attacker exfiltrates session tokens
- Attacker replays tokens from different location/device to access corporate data
- Even with MFA enabled, the attack succeeds because the session is already authenticated
How Legba stops session hijacking:
- User authenticates to corporate SaaS application through Legba
- Authentication happens in the isolated container:
- Session tokens created in isolated environment
- Cookies stored only in isolated browser instance
- Local credential stores never accessed
- If attacker compromises the isolated container:
- Can steal tokens from the isolated environment
- But those tokens exist only in the ephemeral container
- Cannot access tokens from user's actual browser
- Cannot access locally stored credentials
- Container destroyed when session ends:
- All stolen tokens erased
- No persistent access for the attacker
- Next session uses entirely new tokens
The result: Even if an attacker successfully compromises the isolated container and steals session tokens, those tokens are ephemeral and cannot provide persistent access. More importantly, the attacker never gains access to the user's stored credentials, limiting the scope of compromise.
Phishing and Credential Harvesting (92% Clicked Phishing Links)
The threat: 92% of users clicked a phishing link within the last year. Sophisticated phishing sites impersonate legitimate authentication pages with incredible accuracy, harvesting credentials from even security-aware users.
How Legba stops phishing:
- User receives phishing email with convincing fake Microsoft login page
- User clicks link while protected by Legba
- Phishing site loads in isolated container
- User enters credentials on the fake site:
- Credentials entered in isolated environment
- Legba can monitor inputs and detect suspicious authentication requests
- Security team alerted when user attempts to enter credentials on suspicious site
- Even if credentials are submitted:
- They're submitted from the isolated container
- User's real credential store never accessed
- Local password manager data never exposed
- Attacker gets credentials entered manually, but not stored credentials
The result: Phishing still works (users will always click), but the blast radius is contained. The attacker might harvest manually-entered credentials, but they can't access the user's password manager, stored authentication tokens, or local credential stores. Combined with security team alerts, this transforms phishing from a catastrophic breach into a manageable security event.
Zero Trust Integration: Policy-Based Isolation
Legba doesn't just isolate blindly. The platform integrates deeply with Zero Trust architecture principles to enforce granular, context-aware isolation policies.
Centralized Policy Management Dashboard
Your security team configures isolation policies from a centralized management console. This isn't a configuration file or command-line interface; it's a comprehensive policy engine that enforces security across your entire organization.
Policy configuration capabilities:
Application and website classification:
- Define which applications require isolation (all external sites, specific categories, individual domains)
- Whitelist trusted internal applications that don't require isolation
- Classify applications by risk level (high-risk external sites always isolated)
- Integrate threat intelligence feeds for real-time risk classification
Identity-centric access controls:
- Different isolation policies for different user roles (executives get stricter isolation)
- Privileged account holders automatically isolated
- Contractors and third-party users always isolated
- Guest access requires isolation by default
Contextual policy enforcement:
- Device posture: Unmanaged devices automatically isolated
- Location-based policies: Users outside corporate networks isolated
- Time-based policies: After-hours access requires enhanced isolation
- Network context: Public WiFi triggers automatic isolation
Performance: Why Legba Doesn't Slow You Down
The fatal flaw of traditional remote browser isolation is latency. Security teams love it. Users hate it. And what users hate, they disable.
Legba's edge-based architecture solves this problem at the architectural level.
The Traditional RBI Latency Problem
Traditional remote browser isolation centralizes execution in cloud data centers. The physics of distance creates unavoidable latency:
Latency sources in centralized RBI:
- Geographic distance: User in San Francisco, RBI data center in Virginia = 70ms round trip time minimum
- Processing overhead: Fetching the website, rendering it, compressing the video stream adds 50-150ms
- Network congestion: Shared infrastructure creates variable latency spikes
- Streaming compression/decompression: Video encoding/decoding adds 20-50ms
- Interactive elements: Every click, keystroke, or scroll requires a round trip to the data center
Total latency: 200-500ms added to every interaction
Users notice. Pages feel sluggish. Videos buffer. Forms lag. The security is perfect, but the user experience is degraded enough that productivity suffers.
Legba's Solution: Edge-Based Processing
Legba's distributed edge architecture minimizes latency to imperceptible levels:
Edge node proximity:
- Edge nodes positioned in major metropolitan areas
- Typical distance to nearest edge node: 10-50 miles
- Typical round-trip time: 5-20ms (vs. 70-200ms for centralized RBI)
User experience metrics:
- Latency overhead: <20ms added latency (vs. 200-500ms for traditional RBI)
- Visual quality: Pixel-perfect rendering at 60fps
- Interactive elements: Indistinguishable from native browsing
- Video playback: Smooth streaming without buffering
- Form inputs: Immediate feedback, no typing lag
"Invisible by Design": Protection Without Friction
The goal isn't just to be fast enough. The goal is to be completely unnoticeable.
What users experience:
- Browsing feels exactly like native browsing
- No perceptible lag or delay
- Videos play smoothly
- Interactive elements respond immediately
- No visual artifacts or compression quality loss
What's actually happening:
- Every web request is intercepted
- Evaluated against security policies
- Redirected to edge-based isolation
- Executed in ephemeral container
- Streamed back as safe pixels
- All in the time it would take to load the page normally
This is the difference between a security solution users tolerate and one they never notice. Legba's architecture delivers absolute security with zero user friction.
Real-World Use Cases: Where Legba Makes the Difference
BYOD and Unmanaged Devices
The challenge: 82% of organizations allow BYOD to some extent, while 92% of ransomware attacks in 2024 involved unmanaged devices. Users on unmanaged devices are 71% more likely to face malware.
How Legba solves this:
Legba isolates browsing regardless of device security posture. It doesn't matter if the device has antivirus, if it's running outdated software, or if it's infected with malware. All web browsing happens in isolated containers at the edge, not on the device.
The result: Secure BYOD without device management complexity. You're not trying to secure the device (impossible); you're securing the browsing sessions (architecture-level guarantee).
High-Risk User Populations
The challenge: Executives, privileged account holders, and high-value targets face disproportionate risk from sophisticated attacks. Attackers specifically target these users because compromising them provides maximum value.
How Legba solves this:
Automatic isolation for high-risk users without any change to their browsing experience. They don't know they're protected differently; they just browse normally while Legba enforces stricter isolation behind the scenes.
The result: Executives get the highest level of protection without any user experience degradation. They browse normally. Legba protects them invisibly.
Legba vs. Traditional Security: What Changes
Let's directly compare security postures before and after Legba deployment.
Before Legba: Defense in Depth That's Full of Holes
Traditional security stack:
- Antivirus/Anti-malware: Detects known malware signatures. Can't detect: Zero-day exploits, browser-native ransomware, polymorphic threats
- Firewall: Blocks unauthorized network connections. Can't inspect: Encrypted HTTPS traffic
- VPN: Encrypts network traffic. Doesn't protect against: Threats that travel inside the encrypted tunnel
- EDR: Monitors endpoint for suspicious behavior. Can't prevent: Initial compromise; only detects after the fact
Attack scenario without Legba:
- User receives phishing email with link to weaponized site
- Email filter doesn't block it (hosted on legitimate cloud infrastructure)
- User clicks link
- Website exploits zero-day browser vulnerability
- Antivirus doesn't detect it (zero-day, no signature)
- Malware executes on endpoint
- EDR eventually detects suspicious behavior
- But the compromise already happened
With Legba: Architecture-Level Prevention
Attack scenario with Legba:
- User receives phishing email with link to weaponized site
- Email filter doesn't block it (same as before)
- User clicks link
- Legba intercepts and isolates the request
- Website loads in isolated container at the edge
- Website exploits zero-day browser vulnerability
- Exploit succeeds in the isolated container
- Malware executes in isolated environment
- User closes tab, container destroyed, malware erased
- Endpoint never compromised
| Attack Vector | Before Legba | With Legba |
|---|---|---|
| Zero-day exploits | Antivirus can't detect, EDR detects post-compromise | Exploit executes in isolation, never reaches endpoint |
| Browser-native ransomware | Bypassed all antivirus (proven in research) | Encrypts virtualized file system, real files untouched |
| Phishing | Relies on user awareness training (92% still clicked) | Credentials entered in isolation, real credential stores protected |
| Session hijacking | MFA bypassed once tokens stolen | Tokens exist only in ephemeral containers |
| Malicious extensions | Can harvest local credentials and passwords | Extensions run in isolation, no access to local data |
| Drive-by downloads | Malware downloads to endpoint, antivirus tries to detect | Downloads to isolated file system, destroyed with container |
The Fundamental Shift: Prevention Instead of Detection
Traditional security is based on detection: identify malicious behavior and block it. This creates an arms race where attackers constantly develop new techniques to evade detection.
Legba is based on prevention through isolation: don't try to distinguish malicious from benign; just execute everything in isolation so malicious code can't cause harm.
Detection-based security:
- Requires knowing what malicious behavior looks like
- Constantly playing catch-up with new attack techniques
- Always vulnerable to zero-days and unknown threats
- Generates false positives and false negatives
Isolation-based security:
- Doesn't need to distinguish malicious from benign
- Works against unknown and future threats
- Zero-days can't compromise endpoints (executes in isolation)
- No false positives (everything isolated equally)
- No false negatives (architecture prevents compromise)
Conclusion: The Architecture That Actually Works
The browser security problem is not a detection problem. It's an architecture problem.
Traditional security tries to detect and block malicious code before it executes. This approach fundamentally fails against:
- Zero-day exploits that have no signatures
- Browser-native ransomware that looks like legitimate browser API usage
- Polymorphic extensions that impersonate legitimate tools
- Sophisticated phishing that evades filters
- Session hijacking that happens after authentication
No amount of machine learning, threat intelligence, or behavioral analysis can solve an architecture problem. If malicious code can execute on your endpoints, it will eventually succeed in compromising them.
The only architecture that works is isolation.
Legba's browser-native isolation doesn't try to detect threats. It doesn't try to distinguish malicious from benign. It executes everything in isolated, ephemeral containers at the edge, ensuring that even successful attacks cannot compromise your actual systems.
The technical innovations that make this possible:
- Edge-based execution: Distributed architecture delivers native performance while maintaining complete isolation
- Ephemeral containers: Every session starts clean and ends completely, preventing persistence
- Pixel-perfect streaming: Users experience native browsing while all code executes remotely
- Application-agnostic isolation: Protection extends beyond browsers to any application requiring secure access
- Policy-based enforcement: Granular controls based on identity, context, and risk
The result is a security architecture where:
- Zero-day exploits execute in isolation and cannot reach your systems
- Ransomware encrypts disposable file systems that vanish after sessions
- Phishing sites harvest credentials from containers, not your credential stores
- Malicious extensions run in isolation without access to local data
- Session tokens exist only in ephemeral environments
- Drive-by downloads save to virtualized file systems that get destroyed
And most importantly: users never notice. The protection is invisible. The performance is native. The user experience is unchanged.
This is security that actually works in 2025, when 85% of work happens in browsers and 60% of breaches originate there. Traditional security failed to address this reality. Legba's browser-native isolation succeeds because it changes the architecture, not just the detection algorithms.
The browser-centric workplace demands browser-centric security.
Learn More
Ready to see how Legba's browser-native isolation can protect your organization?
- Request a demo: See Legba in action with real-world attack scenarios
- Read the white paper: Deep dive into the research and threat landscape
- Talk to our team: Discuss your specific use cases and deployment requirements
Visit legba.app to get started.
Frequently Asked Questions
Q: How is browser-native isolation different from Chrome's built-in sandboxing?
A: Chrome's sandboxing isolates different tabs and processes from each other within the browser, but all execution still happens on your device. If a zero-day exploit breaks out of the sandbox (which has happened), your device is compromised. Legba executes all browsing in isolated containers at the edge, so even if an exploit breaks out of Chrome's sandbox, it's breaking out within the isolated container, not on your actual device.
Q: Does Legba slow down my browsing?
A: No. Legba's edge-based architecture adds less than 20ms of latency, which is imperceptible to users. Traditional RBI can add 200-500ms, which users notice. Our pixel-perfect streaming technology delivers native browsing performance.
Q: Can users tell they're being protected by Legba?
A: No. That's the point of "Invisible by Design." The browsing experience is indistinguishable from native browsing. Users don't see additional prompts, warnings, or slowdowns. The protection happens transparently.
Q: What happens if the edge node goes down?
A: Legba's distributed architecture provides automatic failover. If your primary edge node becomes unavailable, your session automatically fails over to an alternate edge node. Most failovers happen without users even noticing.
Q: How does Legba handle file downloads?
A: Files downloaded in isolated sessions can be scanned and sanitized before being transferred to the user's device. You can also configure policies to block downloads entirely from high-risk sites, or allow downloads only for specific file types.
Q: How long does deployment take?
A: For organizations using Google Workspace, deployment can happen in hours. You install the Chrome extension via centralized policy, configure your isolation policies in the management console, and protection begins immediately. No network changes, no infrastructure procurement, no lengthy implementation projects.
Q: Can Legba replace my VPN?
A: Legba provides secure access to internal web applications without requiring VPN, making it a VPN alternative for many use cases. However, VPNs provide network-level access for non-web applications, so the two technologies are complementary rather than mutually exclusive. Many organizations use Legba to reduce VPN usage for web-based access while maintaining VPN for specific legacy applications.
Q: How does Legba handle single sign-on (SSO)?
A: Legba integrates with your existing SSO infrastructure (Okta, Azure AD, Google Workspace, etc.). Users authenticate once with your SSO, and Legba enforces isolation based on their verified identity.